OpenSCAP is an open-source project. It is very useful tool for checking security compliance by running security standards against a system. It uses SCAP The Security Content Automation Protocol (SCAP) provides an automated, standardized methodology for managing system security, including measuring and managing system vulnerability, and evaluating policy compliance against security standards such as the Federal Information Security Management Act (FISMA). The U.S. government content repository for SCAP standards is the National Vulnerability Database (NVD), which is managed by the National Institute of Standards and Technology (NIST).
I will go over how to install OpenSCAP on Oracle Linux 7 & how to use oscap command in this post. Let’s install scap-secutiry-guide package.
# yum install scap-security-guide -y
This packages will provide system-hardening guidance in SCAP format and security profiles. It also includes Security Technical Implementation Guide (STIG) profiles (draft versions) aligned with Defense Information Systems Agency (DISA) STIG for Oracle Linux. You can download DISA verified STIG from DISA site https://public.cyber.mil/stigs/downloads/?_dl_facet_stigs=operating-systems%2Cunix-linux.
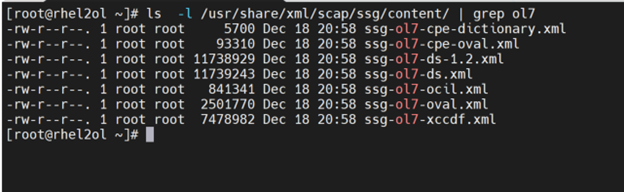
STIG profiles can be found under /usr/share/xml/scap/ssg/content directory.
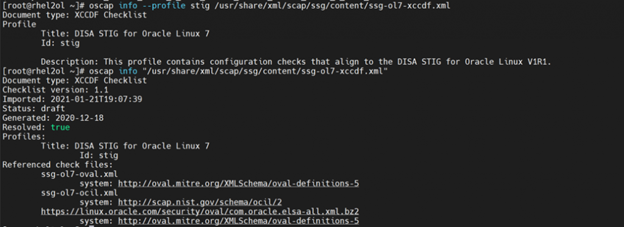
To get details on any STIG run “oscap info” command.
To evaluate host against STIG profile, run “oscap xccdf eval” command as shown here.
#oscap xccdf eval –profile stig –results /tmp/hostname-ssg-results.xml –report /tmp/hostname-ssg-results.html –cpe /usr/share/xml/scap/ssg/content/ssg-ol7-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-ol7-xccdf.xml
There will be couple of reports generated as a result of above command.
![]()
Review html report for details on all checks performed and their results. Couple of snapshots are provided here.
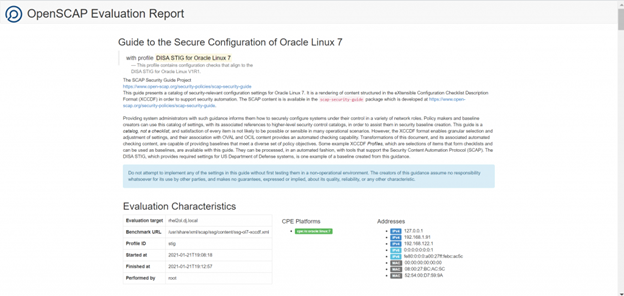
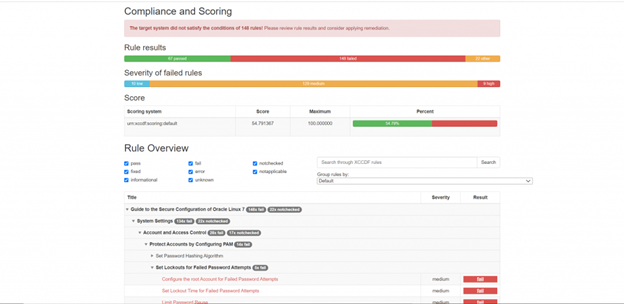
You can also fix all issues by including “–remediate” flag to oscap command. Following command will evaluate host against STIG profile first and then start fixing all issues. You may see that some types of issues cannot be fixed like disk/partition level changes etc. They will need manual intervention.
oscap xccdf eval –remediate –profile stig –results /tmp/hostname-ssg-results.xml –cpe /usr/share/xml/scap/ssg/content/ssg-ol7-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-ol7-xccdf.xml
To create bash script for recommended fixes to review and run later, execute following.
oscap xccdf generate fix –fix-type bash –profile stig –output /tmp/my-remediation-script.sh /usr/share/xml/scap/ssg/content/ssg-ol7-xccdf.xml
Review remediation script for all fixes that will be applied to the system. If necessary make changes to the script as well.